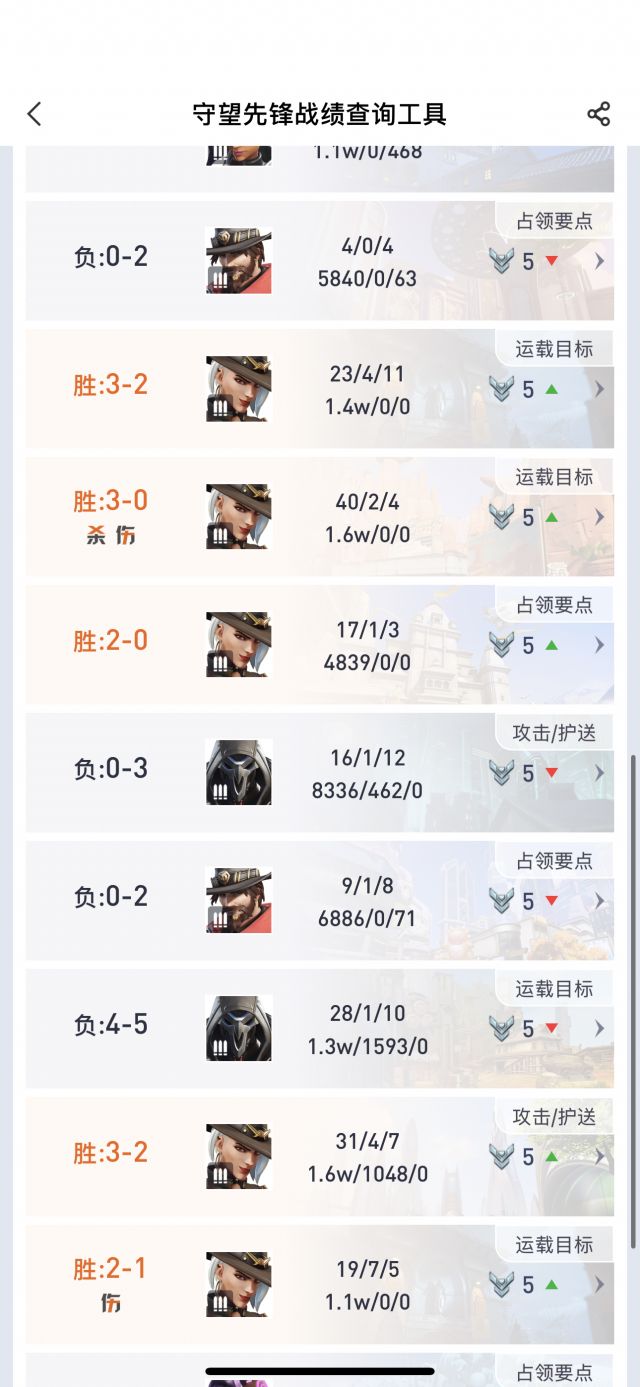
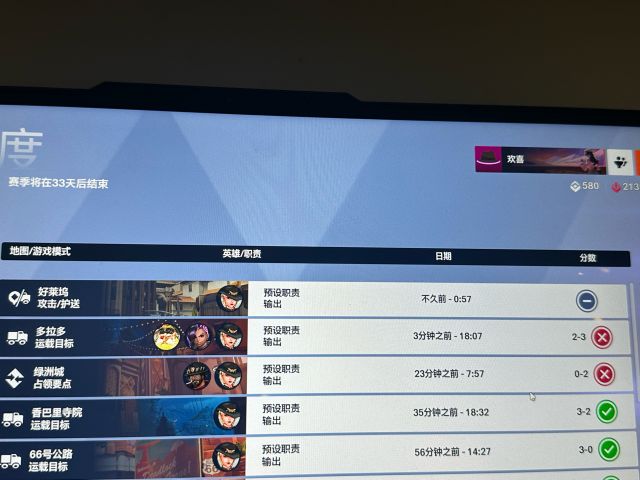
刚才一个寺庙图,毛妹吃了没有10个也有8个的西格玛石头
你说他,他回你一句,怪我
🖼 12个月大的婴儿也能形成短时记忆 长期以来,科学界普遍认为婴儿在三四岁之前大脑尚未发育成熟,无法形成持久记忆。然而近日发表于《科学》(Science)的一...
12个月大的婴儿也能形成短时记忆
长期以来,科学界普遍认为婴儿在三四岁之前大脑尚未发育成熟,无法形成持久记忆。然而近日发表于《科学》(Science)的一项研究中研究人员发现,年仅12个月的婴儿也具备形成至少持续几分钟记忆的能力。
为验证婴儿记忆能力,研究团队开发了一种专为婴儿设计的功能性磁共振成像(fMRI)技术,并在测试过程中允许家长与婴儿互动,以确保婴儿在舒适状态下完成扫描任务。研究对象包括26名年龄在4个月至2岁之间的婴儿。结果显示,当婴儿首次看到一张图像时,如果其海马体活动增强,则在之后再次看到该图像时,他们会注视更长时间;反之,若海马体在初次观看时未被激活,则注视时间无显著变化。这一反应模式与成人记忆形成过程高度相似。研究还发现,这种记忆反应在12个月以上的婴儿中尤为明显,显示出随着年龄增长,海马体功能逐步增强。
研究人员指出,下一步将继续探讨这些早期记忆的持续性,以及是否存在阻止人们在成年后访问这些记忆的生理机制。
Science News
Science
📮投稿 ☘️频道 🌸聊天

Linux Security Hardening Cache Randomization Was Inadvertently Using The Same Seed
Ahead of the upcoming Linux 6.15 kernel cycle a few early pull requests have already been sent in to Linus Torvalds in advance of the anticipated v6.14 release on Sunday. Among those early changes for Linux 6.15 are the SLAB allocator updates that include a fix for cache randomization with kvmalloc inadvertently being inadequate due to accidentally using the same randomization seed.
With the SLAB pull request ahead of the Linux 6.15 merge window, most notable besides a few minor improvements is improving the kmalloc cache randomization within the kvmalloc code.
Google engineers discovered that the CONFIG_RANDOM_KMALLOC_CACHES hardening feature wasn't properly being employed. CONFIG_RANDOM_KMALLOC_CACHES creates multiple copies of slab caches and makes kmalloc randomly pick one based on the code address in order to help fend off memory vulnerability exploits. But the problem was the same random seed always ended up being used with the current Linux kernel code. From the Google code comments:
Gong Ruiqi of Huawei who worked out the solution to the issue explained:
At least with these pending SLAB updates for the Linux 6.15 merge window, this issue will be resolved and presumably be likely back-ported to existing stable kernels to address this ineffective security hardening.
With the SLAB pull request ahead of the Linux 6.15 merge window, most notable besides a few minor improvements is improving the kmalloc cache randomization within the kvmalloc code.
Google engineers discovered that the CONFIG_RANDOM_KMALLOC_CACHES hardening feature wasn't properly being employed. CONFIG_RANDOM_KMALLOC_CACHES creates multiple copies of slab caches and makes kmalloc randomly pick one based on the code address in order to help fend off memory vulnerability exploits. But the problem was the same random seed always ended up being used with the current Linux kernel code. From the Google code comments:
"...This is problematic because `__kmalloc_node` will use the return address as the seed to derive the *random* cache to use. Since all calls to `kvmalloc_node` will use the same seed when the size is large, the hardening is rendered completely pointless."
Gong Ruiqi of Huawei who worked out the solution to the issue explained:
"That literally means all kmalloc invoked via kvmalloc would use the same seed for cache randomization (CONFIG_RANDOM_KMALLOC_CACHES), which makes this hardening non-functional.
The root cause of this problem, IMHO, is that using RET_IP only cannot identify the actual allocation site in case of kmalloc being called inside non-inlined wrappers or helper functions. And I believe there could be similar cases in other functions. Nevertheless, I haven't thought of any good solution for this. So for now let's solve this specific case first.
For __kvmalloc_node_noprof, replace __kmalloc_node_noprof and call __do_kmalloc_node directly instead, so that RET_IP can take the return address of kvmalloc and differentiate each kvmalloc invocation."
At least with these pending SLAB updates for the Linux 6.15 merge window, this issue will be resolved and presumably be likely back-ported to existing stable kernels to address this ineffective security hardening.
Enthusiasts report Gigabyte X870E Aorus Xtreme chipset temps exceeding 100°C
Multiple reports suggest a potential manufacturing flaw in Gigabyte's premium X870E Aorus Xtreme AI TOP motherboard, leading to uneven contact between the chipset and the heatsink.
[新闻] 《守望先锋》英雄游戏预览:芙蕾娅
[quote]

[flash]https://www.bilibili.com/video/av114201251087400[/flash]
全新输出英雄弗蕾娅登场,狩猎开始!
弗蕾娅曾是守望先锋最负盛名的搜救干员,如今却凭借着无可匹敌的技艺与精准无比的爆炸火力,踏上了赏金猎人之路。
手持标志性速射弩,具有高机动性技能组的弗蕾雅能在远程与空中战斗中大显身手,让对手陷入难以摆脱的战术噩梦。
即日起至3月25日,弗蕾娅限时试玩开启,她将在第16赛季正式上线。
特别感谢芙蕾娅的配音演员:唐雅菁
[/quote]

[flash]https://www.bilibili.com/video/av114201251087400[/flash]
全新输出英雄弗蕾娅登场,狩猎开始!
弗蕾娅曾是守望先锋最负盛名的搜救干员,如今却凭借着无可匹敌的技艺与精准无比的爆炸火力,踏上了赏金猎人之路。
手持标志性速射弩,具有高机动性技能组的弗蕾雅能在远程与空中战斗中大显身手,让对手陷入难以摆脱的战术噩梦。
即日起至3月25日,弗蕾娅限时试玩开启,她将在第16赛季正式上线。
特别感谢芙蕾娅的配音演员:唐雅菁
[/quote]
[亞洲無碼] 探花欧阳克酒店约炮御姐范穿旗袍的小姐姐拥有跟身体不协调的肥臀后入视觉效果极佳又骚又浪[116/MP4/802MB]
【影片格式】:MP4
【影片大小】:802MB
【影片时间】:00:28:20
【影片说明】:无码
【影片截图】:











下载地址:
https://www.116pan.com/viewfile.php?file_id=330860
【影片大小】:802MB
【影片时间】:00:28:20
【影片说明】:无码
【影片截图】:











下载地址:
https://www.116pan.com/viewfile.php?file_id=330860
[亞洲無碼] 原档泄密流出长春清纯白嫩美乳女大学生和男友自拍性爱视频[116/MP4/385MB]
【影片格式】:MP4
【影片大小】:384MB
【影片时间】:00:10:53
【影片说明】:无码
【影片截图】:









下载地址:
https://www.116pan.com/viewfile.php?file_id=330859
【影片大小】:384MB
【影片时间】:00:10:53
【影片说明】:无码
【影片截图】:









下载地址:
https://www.116pan.com/viewfile.php?file_id=330859
[亞洲無碼] 2025年3月最新富二代真实约炮【fKabuto】拿下几个学生妹,都完美露脸,蜜桃臀圆润白皙,后入啪啪享受少女的美好![116/MP4/771MB]
【影片大小】:771M
【影片时间】:00:15:40
【影片说明】:无码
【影片截图】:


















【下载地址】:
https://www.116pan.com/viewfile.php?file_id=329796
【影片时间】:00:15:40
【影片说明】:无码
【影片截图】:


















【下载地址】:
https://www.116pan.com/viewfile.php?file_id=329796